Portfolio Planning
Help Center: SSO Configuration (Azure AD)
What is SSO?
Single Sign-On (SSO) is an authentication process that enables users to access multiple applications or systems with a single set of login credentials, simplifying the sign-in process and enhancing user experience. In the context of "Joiners, Movers, Leavers" (JML), SSO plays a crucial role in managing user permissions efficiently, ensuring that new employees gain timely access, current employees have their permissions adjusted as they move roles, and departing employees have their access promptly revoked, thereby maintaining security and compliance throughout the user lifecycle.
How does SSO work?
The most prevalent configuration employs Just-In-Time (JIT) access provisioning through SAML, with granular permissions managed within Kiplot.
In layman's terms, your Identity and Access Management (IAM) solution (e.g., Azure AD) maintains a group named "Kiplot Access." When a user attempts to authenticate with Kiplot, the platform verifies the user's permissions via SAML to determine if they are authorized to access Kiplot. If the user has the appropriate permissions and has never accessed Kiplot before, an account is created for them using the JIT method. If the user has previously accessed Kiplot, they are authenticated into their existing account, including any assigned permissions.
Do you support token encryption for SSO?
Yes. Note that this is optional.
Is there an Azure gallery app?
No – Kiplot must be created as a custom application, however configuration is extremely straightforward.
Can I prevent users from logging in without SSO?
Yes – though this must be configured by Kiplot support. Please make sure you let your Activation Lead know that you want this set up.
Can I allow users to log in via SSO and directly to Kiplot without SSO?
Yes. If you wish, parts of your user population may authenticate via SSO, and parts may authenticate directly with Kiplot. However, we advise for security reasons to require all users to login via SSO.
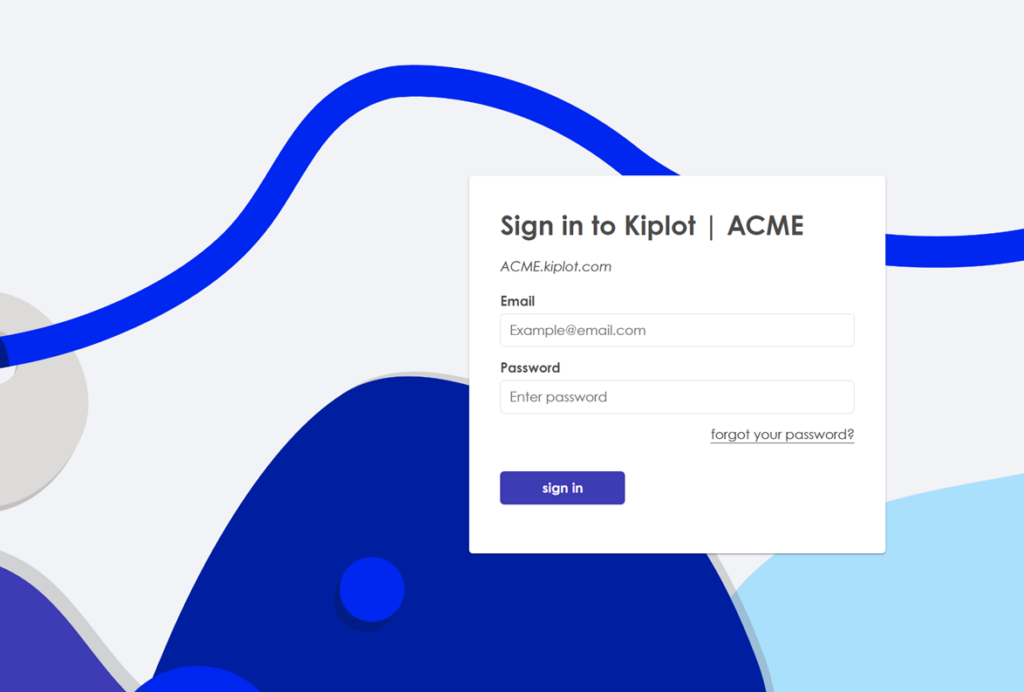
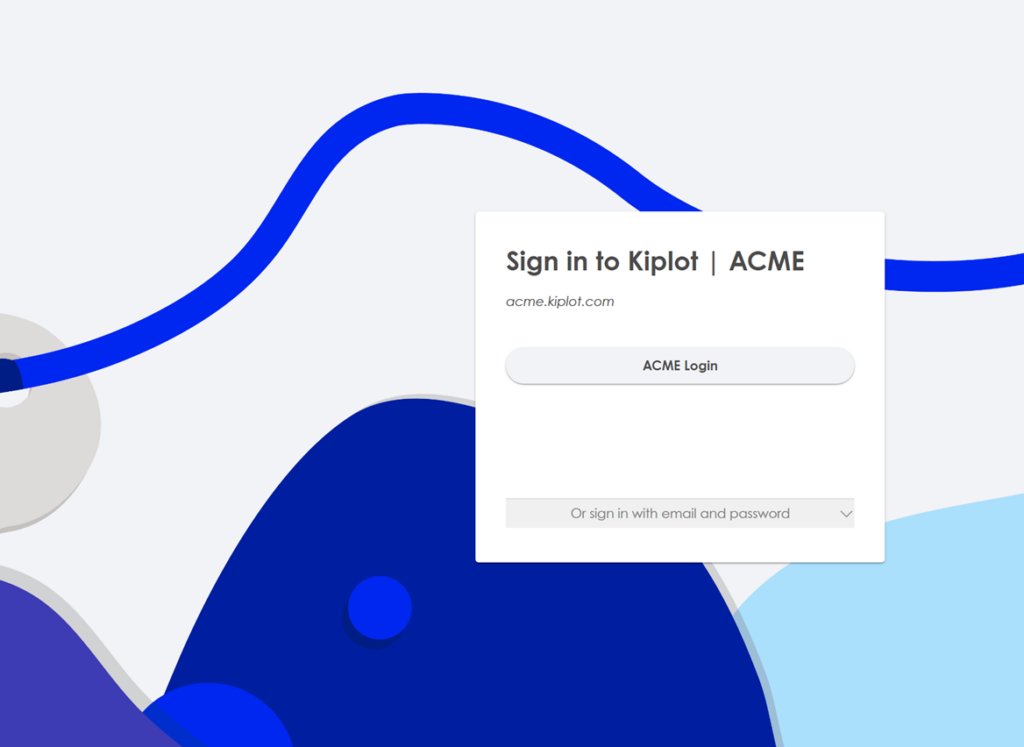
How will the login experience change for users before and after configuring SSO?
Before SSO
After SSO
Step by Step instructions
- Request your service provider metadata file from Kiplot. This will include:
- Identifier (Entity ID)
- Reply URL (Assertion Consumer Service URL)
- Sign on URL
- Login to the Azure Portal:
- Navigate to the Azure Portal and sign in with an account that has been assigned at least the User administrator role in the Azure AD organization.
- Choose Azure Active Directory:
- In the left-hand navigation pane, click on "Azure Active Directory" service.
- Enterprise Applications:
- In the Azure AD blade, click on "Enterprise applications" from the menu.
- New Application:
- Click on "+ New application" at the top.
- In the "Add from the gallery" section, choose "Non-gallery application".
- Name the application, “Kiplot”.
- Configure Single Sign-On:
- Once the application is created, click on the "Single sign-on" from the application's left-hand navigation menu.
- Choose the "SAML" option.
- SAML-based Sign-on Settings:
You'll have to set up a few things here:
- Basic SAML Configuration:
Use the information below to complete this section. Note that you must replace
[yourdomain]with the name of the subdomain that has been assigned to your organisation’s Kiplot instance.
- User Attributes & Claims:
Required Claim
This should be correct by default, but please make sure that within “Attributes and Claims” under “Required Claim”, the following is set up. Note that in this example, user.userprincipalname is their email (which is typically the case). If it is different for your organisation, please select the correct value for email.
- Unique User Identifer (Name ID) → user.userprincipalname
Additional Claims (optional)
givenname → user.givenname
surname → user.surname
emailaddress → user.mail
name → user.userprincipalname
Unique User Identifier → user.userprincipalname
- Visit the “Properties” section in the left hand nav bar and update the logo for the Kiplot Application. You can download the Kiplot Logo from this link: https://www.kiplot.com/kiplot-azure-ad-logo/
- Basic SAML Configuration:
Use the information below to complete this section. Note that you must replace
- Download the XML Metadata file:
- In the same "Single sign-on" SAML configuration page, scroll down to the "SAML Signing Certificate" section.
- Click on "Federation Metadata XML" – "Download" to get the XML file. This is the file you'll need to share back with Kiplot.
- Share XML file back with Kiplot
- We will confirm once SSO has been configured
- Please identify a user to act as tester
The Kiplot Help Center is currently in ALPHA. It is actively under development.

